SQL Injection
An SQL injection is a form of cyberattack that targets database-linked websites and web applications. These attacks exploit poorly-configured website and database server software to trick a server into parsing SQL statements it otherwise would not carry out. These attacks may reveal sensitive personal and financial information, allow an attacker to change or delete information stored in a database, or provide other unauthorized access.
A website is vulnerable to an SQL injection when it accepts user input from a text form and includes it as part of an SQL query. Instead of filling out the form field with expected information (like a username), the attacker enters a text string that modifies the SQL query. For example, a hypothetical query might start with SELECT UserID, Name, Password FROM Users WHERE UserID = , followed by the input from a User ID form field. If the user enters their User ID, the query works as expected and pulls up their information.
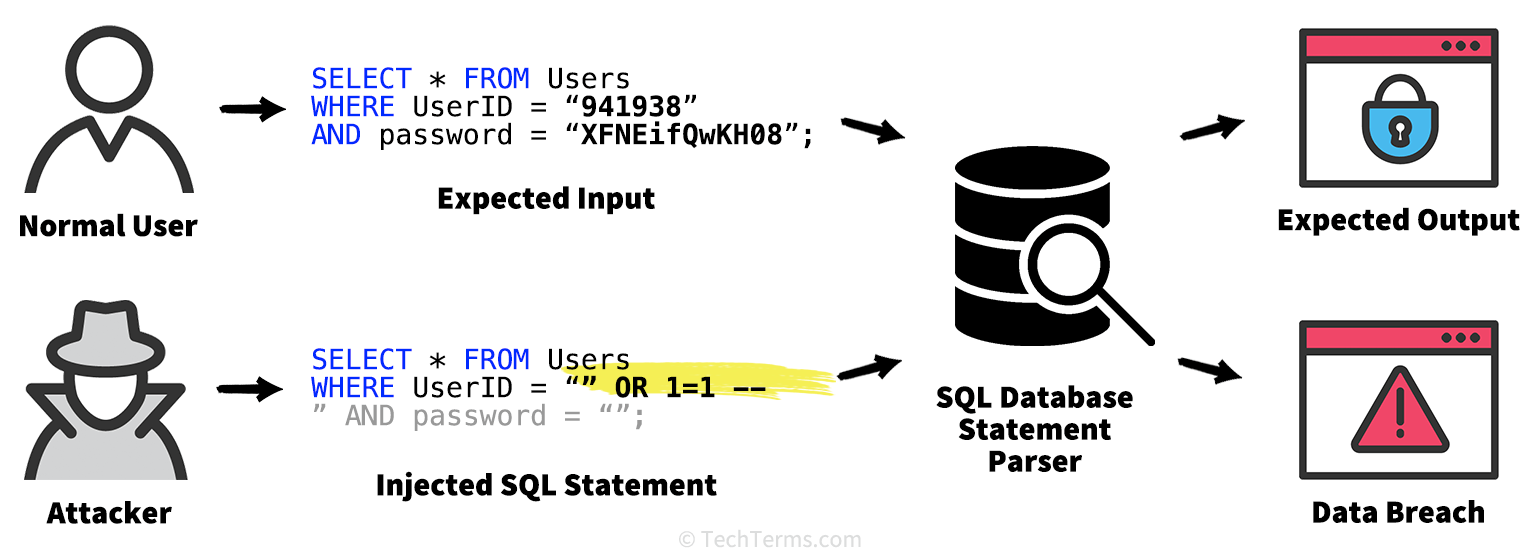
However, if the server inserts input text into the query unrestricted, an attacker can use it to modify the SQL query statement itself. If instead of a User ID, someone enters the text 317 OR 1=1, the query becomes SELECT UserID, Name, Password FROM Users WHERE UserID = 317 OR 1=1;. Since OR 1=1 always resolves true, it overrides the User ID; the query instead returns the User IDs, names, and passwords of all entries in the Users table. Other types of code injection may allow an attacker to log in as a site administrator, delete records or tables from a database, or (in some extreme cases) inject and run shell scripts and other code.
A website administrator can prevent SQL injection attacks by keeping the server software up to date. It is also important to "sanitize" database inputs by restricting input text or by filtering out certain characters. Website administrators may also parameterize their SQL queries — using placeholders in the query that refer to the user input instead of inserting it directly into the query.
 Test Your Knowledge
Test Your Knowledge