WPA
Stands for "Wi-Fi Protected Access."
WPA is a security protocol for creating secure Wi-Fi networks. It was introduced in 2004 to replace the previous security protocol, WEP, due to vulnerabilities in WEP's encryption method. WPA uses 256-bit encryption and is considered the minimum standard for wireless network security, supported by all Wi-Fi-certified devices since 2006. Later generations (WPA2 and WPA3) are even more secure.
WPA uses encryption to protect traffic over wireless networks from eavesdropping. Both sides of a wireless connection need to use the same encryption/decryption key. WEP was vulnerable to eavesdropping because it used the same encryption key for each data packet that traveled over a network. WPA uses a technique called Temporal Key Integrity Protocol (TKIP) to generate a new encryption key for each data packet, making it more secure than WEP.
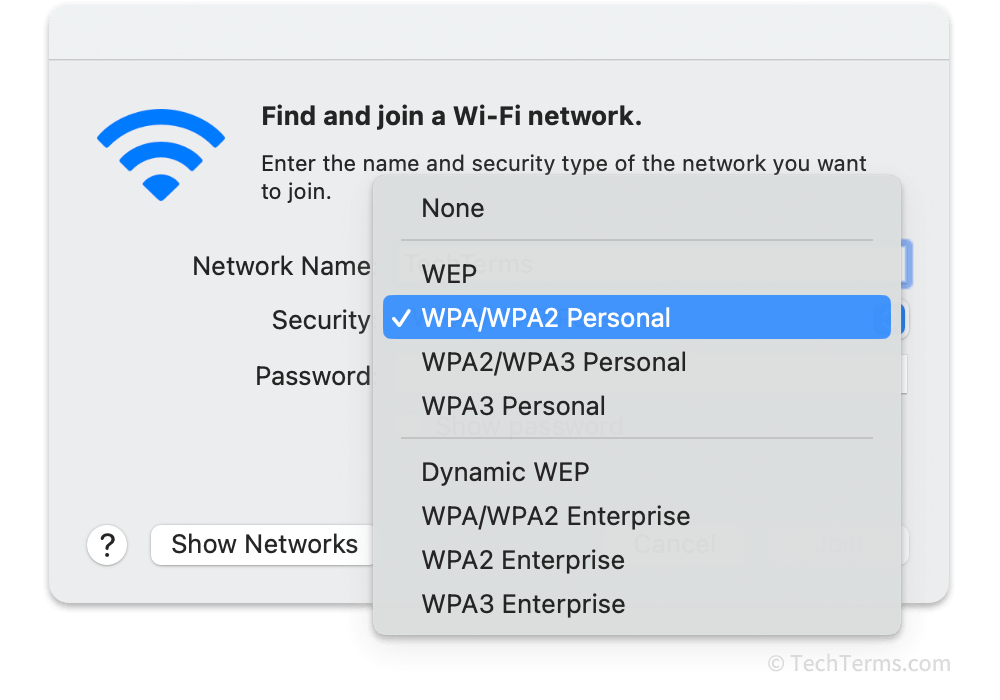
The WPA specification supports two operation modes: WPA-Personal and WPA-Enterprise. WPA-Personal uses a pre-shared key for encryption; this key also functions as the Wi-Fi network's passphrase. Every device that connects to a WPA-Personal network uses the same passphrase, and changing that passphrase requires every client to update their settings. WPA-Enterprise instead uses an authentication server to validate each user's unique login credentials. A WPA-Enterprise access point generates a new encryption key each time a user connects to the network.
The developers of WPA, the Wi-Fi Alliance industry group, intended for devices designed for WEP to receive firmware updates to add support for WPA. Running on the same hardware as WEP limited the computational resources available to WPA encryption. While WPA is more secure than WEP, it is still vulnerable to attacks that can decrypt data packets encrypted using TKIP. Access points designed for WPA2 have more powerful hardware, allowing them to use the more secure Advanced Encryption Standard (AES) encryption method.
 Test Your Knowledge
Test Your Knowledge